Cloudflare
Cloudflare, Inc. is an American content delivery network and DDoS mitigation company,[3] founded in 2009. It primarily acts as a reverse proxy between a website’s visitor and the Cloudflare customer’s hosting provider.[4][5] Its headquarters are in San Francisco, California.[3] According to The Hill, it is used by more than 20 percent of the entire Internet for its web security services.[6]
Cloudflare was founded in July 2009 by Matthew Prince, Lee Holloway, and Michelle Zatlyn.[1][7][8][9] Prince and Holloway had previously collaborated on Project Honey Pot, a product of Unspam Technologies that served as some inspiration for the basis of Cloudflare.[10] From 2009, the company was venture-capital funded.[11] On August 15, 2019, Cloudflare submitted its S-1 filing for IPO on the New York Stock Exchange under the stock ticker NET.[12] It opened for public trading on September 13, 2019 at $15 per share.[13]
In 2020, Cloudflare co-founder and COO Michelle Zatlyn was named president, making her one of the few woman presidents of a publicly traded technology company in the U.S.[14]
Cloudflare has acquired web-services and security companies, including StopTheHacker (Feb 2014),[15] CryptoSeal (June 2014),[16] Eager Platform Co. (December 2016),[17] Neumob (November 2017),[18] S2 Systems (January 2020),[19] Linc (December 2020),[20] Zaraz (December 2021),[21] Vectrix (February 2022),[22] and Area 1 Security (February 2022).[23]
Since at least 2017, Cloudflare has been using a wall of lava lamps in their San Francisco headquarters as a source of randomness for encryption keys, alongside double pendulums in its London offices and a geiger counter in its Singapore offices.[24] The lava lamp installation implements the Lavarand method, where a camera transforms the unpredictable shapes of the “lava” blobs into a digital image.[25][24]
Claims regarding DDoS mitigation[edit]
Cloudflare received media attention in June 2011 for providing DDoS mitigation for the website of LulzSec, a black hat hacking group.[26]
In March 2013, The Spamhaus Project was targeted by a DDoS attack that Cloudflare reported exceeded 300 gigabits per second (Gbit/s).[27][28] Patrick Gilmore, of Akamai, stated that at the time it was “the largest publicly announced DDoS attack in the history of the Internet.” While trying to defend Spamhaus against the DDoS attacks, Cloudflare ended up being attacked as well; Google and other companies eventually came to Spamhaus’ defense and helped it to absorb the unprecedented amount of attack traffic.[29]
In February 2014, Cloudflare claimed to have mitigated an NTP reflection attack against an unnamed European customer, which they stated peaked at 400 Gbit/s.[30][31] In November 2014, it reported a 500 Gbit/s DDoS attack in Hong Kong.[32] In June 2020, it mitigated a DDoS attack that peaked at 250 Gbit/s.[33] In July 2021 the company claimed to have absorbed a DDoS attack three times larger than any they’d previously recorded, which their corporate blog implied was over 1.2 Tbit/s in total.[34]
Products[edit]
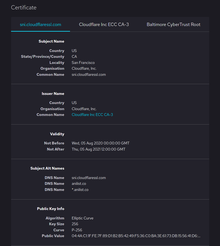
An example of public key certificate issued by Cloudflare
Cloudflare acts as a reverse proxy for web traffic. It supports web protocols including SPDY and HTTP/2, QUIC, and support for HTTP/2 Server Push.[35]
Cloudflare provides DDoS mitigation services that protect customers from distributed denial of service (DDoS) attacks.
In 2010, Cloudflare launched a Content Distribution Network (CDN) service. TechCrunch wrote that its goal was to be “a CDN for the masses”.[36]
In 2017 Cloudflare launched Cloudflare Workers, a serverless computing platform for creating new applications, augmenting existing ones, without configuring or maintaining infrastructure. It has expanded to include Workers KV, a low-latency key-value data store; Cron Triggers, for scheduling Cron jobs; and additional tooling for developers to deploy and scale their code across the globe.[37]
On September 25, 2019, Cloudflare released a freemium VPN service for mobile devices called WARP.[38][39] A year later, beta support for macOS and Windows was released.[40]
As of 2020, Cloudflare was providing DNS services to over 100,000 customers.[41]
In November, 2020, Cloudflare announced Cloudflare for Teams, consisting of a DNS resolver and web gateway called “Gateway,” and a zero-trust authentication service called “Access.”[42]
On May 11, 2022, Cloudflare announced its first SQL database, D1, which is built on SQLite.[43]
On September 26, 2022, Cloudflare announced Zero Trust SIM, an eSIM designed to secure mobile devices and prevent SIM-swapping attacks. The technology is based on the zero trust security model. According to Cloudflare, the secure eSIM can also be used as a second identification factor with 2FA verification protocols. The product will be first available in the United States, with a planned global rollout in the future.[44][45]
In September 2022, Cloudflare began to test Turnstile – an alternative to CAPTCHA. The product, instead of presenting a visual CAPTCHA for the user to solve, automatizes the verification process by conducting JavaScript-based checks inside the browser to determine whether the user is a real person or an automated entity. The algorithm reportedly uses machine learning to optimize the process.[46]
Free services[edit]
In 2014, Cloudflare began providing free DDoS mitigation for artists, activists, journalists, and human rights groups under the name “Project Galileo.”[47] More than 1,000 users and organizations were participating in Project Galileo as of 2020.[48] In 2017, they extended the service to electoral infrastructure and political campaigns under the name “Athenian Project.”[49][50][51] In December 2020, Cloudflare released a beta Jamstack platform for front-end developers to deploy websites on Cloudflare’s infrastructure, under the name “Pages.”[52] In January 2021, the company began providing their “Waiting Room” digital queue product for free for COVID-19 vaccination scheduling under the title “Project Fair Shot.”[53] Project Fair Shot later won a Webby People’s Choice Award in 2022 for Event Management under the Apps & Software category.[54]
Security and privacy issues[edit]
Intrusions[edit]
On June 1, 2012, the hacker group UGNazi redirected visitors to the website 4chan to a Twitter account belonging to UGNazi by “hijacking” 4chan’s domain via Cloudflare. After initiating a password recovery for the Google Workspace hosted email account of Cloudflare CEO Matthew Prince, UGNazi then allegedly used social engineering to trick AT&T support staff into giving them access to his voicemail. Exploiting a bug in Google App’s two-factor authentication security procedures, the hackers allegedly used the voicemail-recovered password to access Prince’s email account without a second layer of authentication. Once in control of Prince’s email account, they were able to redirect the 4chan domain through Cloudflare’s database.[55][56]
In March 2021, Tillie Kottmann from the hacking collective “Advanced Persistent Threat 69420” demonstrated that the group had gained root shell access to security cameras in Cloudflare offices managed by cloud-based physical security company Verkada after obtaining the credentials of a Verkada superuser account that had been leaked on the Internet.[57][58][59][60][61] Cloudflare stated that the compromised cameras were in offices that had been officially closed for several months,[57] though the hacking collective also obtained access to Verkada-operated cameras in Cloudflare’s offices in New York City, London, Austin and San Francisco.[57][61] The hacking group told Bloomberg News that it had video archives from all Verkada customers;[57] it accessed footage from Cloudflare’s cameras and posted a screenshot of security footage which they said was taken by a Verkada camera in a Cloudflare office.[60][62]
Data leaks[edit]
From September 2016 until February 2017, a major Cloudflare bug (nicknamed Cloudbleed) leaked sensitive data, including passwords and authentication tokens, from customer websites by sending extra data in response to web requests.[63] The leaks resulted from a buffer overflow which occurred, according to numbers provided by Cloudflare at the time, more than 18,000,000 times before the problem was corrected.[64][65]
In May 2017, ProPublica reported that Cloudflare routinely discloses the names and email addresses of persons complaining about hate sites to the operators of those sites, which has led to the complainants being harassed. Cloudflare’s general counsel defended the company’s policies by saying it is “base constitutional law that people can face their accusers”, and noted that there had been a disclaimer on Cloudflare’s complaint form since 2015 stating that they “would notify the site owner.”[66] Cloudflare’s CEO later suggested that, had people not wanted their names shared, they should have provided a false name on the reporting form.[67]
Service outages[edit]
There was major outage lasting about 30 minutes, on July 2, 2019 attributed to bad software deployment.[68][69] In 2020, a misconfiguration of a router caused a data pileup and outage in major European cities.[70] Cloudflare experienced another outage in June 2022.[71]
Controversies[edit]
Cloudflare has been criticized for not banning websites with hate speech content. The company has said it has a content neutrality policy and that it opposes the policing of its customers on free speech grounds, except in cases where the customers break the law.[72][73][74] The company has also faced criticism for not banning websites allegedly connected to terrorism groups,[75] but Cloudflare has maintained that no law enforcement agency has asked the company to discontinue these services and it closely monitors its obligations under U.S. laws.[73]
In 2022, a report by Stanford University found that Cloudflare was a prominent CDN provider among several other providers that are disproportionately responsible for serving misinformation websites.[76][77]
Far-right content[edit]
Cloudflare has come under pressure on multiple occasions due to its services being utilized to serve hate speech and far-right content.[78][79][80] As Cloudflare is considered an infrastructure provider, rather than a hosting provider, they are able to maintain broad legal immunity for the content served from their customers.[81]
The Daily Stormer[edit]
Cloudflare provided DNS routing and DDoS protection for the white supremacist and neo-Nazi website, The Daily Stormer. In 2017 Cloudflare stopped providing its services to The Daily Stormer after an announcement on the website asserted that the “upper echelons” of Cloudflare were “secretly supporters of their ideology”.[82][83] Previously Cloudflare had refused to take any action regarding The Daily Stormer.[81] As a self-described “free speech absolutist”, Cloudflare’s CEO Matthew Prince, in a blog post, vowed never to succumb to external pressure again and sought to create a “political umbrella” for the future.[81] Prince further addressed the dangers of large companies deciding what is allowed to stay online, a concern that is shared by a number of civil liberties groups and privacy experts.[84][85][86] The Electronic Frontier Foundation, a US digital rights group, said that services such as Cloudflare “should not be adjudicating what speech is acceptable”, adding that “when illegal activity, like inciting violence or defamation, occurs, the proper channel to deal with it is the legal system.”[82]
Mass shootings and 8chan[edit]
In 2019, Cloudflare was criticized for providing services to the far-right[87] discussion and imageboard 8chan, which allows users to post and discuss content with minimal interference from site administrators. The message board has been linked to mass shootings in the United States and the Christchurch mosque shootings in New Zealand.[87][88][89] In addition, a number of news organizations including The Washington Post and The Daily Dot have reported on the existence of child pornography and child sexual abuse discussion boards.[90][91][92]
A Cloudflare representative stated that the platform “does not host the referenced websites, cannot block websites, and is not in the business of hiding companies that host illegal content”.[93] Cloudflare did not terminate service to 8chan until public and legal pressure mounted in the wake of the 2019 El Paso shooting, a copycat event similar in nature to the Christchurch mosque shootings, in which the associated manifesto was published to 8chan.[94][95][96] In an interview with The Guardian, immediately following the 2019 El Paso shooting, CEO Matthew Prince defended Cloudflare’s support of 8chan, stating that he had a “moral obligation” to keep the site online.[97]
A few days later Cloudflare terminated their service to 8chan, and as a result the website was taken off the clearnet.[98][99]
Kiwi Farms[edit]
Cloudflare provided DDoS mitigation and acted as a reverse proxy for Kiwi Farms, a far-right[100][101] Internet forum dedicated to discussion and trolling of online figures or communities, that often engages in harassment and doxxing of targets,[102] and has been implicated in the suicides of at least three people.[103][104][105][106][107] Kiwi Farms also has a reputation for transphobic content, and its users have been accused of swatting vulnerable individuals.[108][109][110][111] Although Cloudflare was not the primary website host, they did perform critical services to keep Kiwi Farms on-line, both protecting the site from denial-of-service attacks and optimizing content delivery.[112][5][113][114] Kiwi Farms began as a 4chan forum in 2007, but gained notoriety in 2019, when website owner Joshua Moon reposted a video of the Christchurch mosque shootings along with the perpetrator’s manifesto to the Kiwi Farms site. He refused requests for cooperation from New Zealand law enforcement, when asked to provide information regarding users who may have posted relevant information related to the mosque attacks.[115][102]
In 2022, a campaign was launched by transgender activist Clara Sorrenti, who has previously been targeted by the forum, to pressure Cloudflare into terminating service for Kiwi Farms.[116][117] On August 31, 2022, Cloudflare responded to the campaign with a blog post, and likened their services to that of a public utility, stating that “Just as the telephone company doesn’t terminate your line if you say awful, racist, bigoted things, we have concluded … that turning off security services because we think what you publish is despicable is the wrong policy”, but that it would certainly be the “popular choice” to drop sites that the Cloudflare team “personally feels [are] disgusting and immoral”.[118][119] The company also defended their decision by saying that “where they had provided DDoS protection services to an anti-LGBTIQ+ website, they donated 100% of the fees earned to an organisation fighting for LGBTIQ+ rights”.[120] The blog post mentioned Cloudflare’s terms of use agreement, which allows them to terminate service due to “content that discloses sensitive personal information, [and] incites or exploits violence against people” but, according to The Guardian, the statement “did not specifically address how Kiwi Farms users doxxing people did not fall foul of these terms”.[120]
Cloudflare has been accused of pinkwashing their message, by highlighting donations for LGBTQ services like The Trevor Project‘s suicide hotline, with LGBTQ rights organization GLAAD criticizing the statement, calling Cloudflare “the definition of hypocrisy” stating that the company is “hiding behind donations to LGBTQ causes and simultaneously refusing to sever ties with [the Kiwi Farms] website.”[121][122][123]
On September 3, 2022, Cloudflare blocked Kiwi Farms, citing urgent escalating rhetoric against targets of Kiwi Farms, stating that there is an “unprecedented emergency and immediate threat to human life”. According to The Washington Post, there was a “surge in credible violent threats stemming from the site” and CEO Matthew Prince said that Cloudflare believes “there is an imminent danger, and the pace at which law enforcement is able to respond to those threats we don’t think is fast enough to keep up.” Former whistleblower and transgender rights activist Chelsea Manning responded to the situation and said that better long-term solutions are needed for dealing with such “dangerous speech”, suggesting an approach that doesn’t rely on “hosting providers to have to take these things down”.[124][125][126]
Terrorism[edit]
The Huffington Post has documented Cloudflare’s services to “at least 7 terrorist groups”, as designated by the United States Department of State including the Taliban, Al-Shabaab, the al-Aqsa Martyrs’ Brigades, Hamas, Myanmar’s military junta led by the Tatmadaw,[127] and the al-Quds Brigades.[128][129] Cloudflare has been aware since at least 2012, and has taken no action. However, according to Cloudflare’s CEO, no law enforcement agency has asked the company to discontinue these services.[130] Two of the top three online chat forums and nearly forty other web sites belonging to the Islamic State of Iraq and the Levant (ISIL) are guarded by Cloudflare.[130] According to Prince, U.S. law enforcement has not asked Cloudflare to discontinue the service, and it has not chosen to do so itself.[130] In November 2015, hacktivist group Anonymous discouraged the use of Cloudflare’s services following the ISIL attacks in Paris and additional revelations that Cloudflare aids terrorists.[131] Cloudflare responded by calling the group “15-year-old kids in Guy Fawkes masks“, and saying that whenever such concerns are raised it consults anti-terrorism experts and abides by the law.[132]
Crime[edit]
Cloudflare services have been used by Rescator, a carding website that sells stolen payment card data.[133][134][135]
Cloudflare has been cited in reports by The Spamhaus Project, an international spam tracking organization, for the high numbers of cybercriminal botnet operations hosted by Cloudflare.[136][137][138] An October 2015 report found that Cloudflare provisioned 40% of the SSL certificates used by typosquatting phishing sites, which use deceptive domain names resembling those of banks and payment processors to compromise Internet users’ banking and other transactions.[139]
In 2018, Cloudflare was identified by the European Union’s Counterfeit and Piracy Watch List as a “notorious market” which engages in, facilitates, or benefits from counterfeiting and piracy. The report noted that Cloudflare hides and anonymizes the operators of 40% of the world’s pirate sites, and 62% of the 500 largest such sites, and “does not follow due diligence when opening accounts for websites to prevent illegal sites from using its services.”[140][141] Italian courts have enjoined Cloudflare to cease hosting pirate television service “IPTV THE BEST” after it was found to be infringing the intellectual property of Sky Italy and the Italian football league,[142] and German courts have similarly found that “Cloudflare and its anonymization services attract structurally copyright infringing websites.”[143]
Banning of Switter[edit]
In April 2018, Cloudflare dropped Switter as a client and ceased services. Switter was a social media network for the sex worker community, built on Mastodon‘s open-source software and was launched in March of 2018, with 49,000 members joining in the first few weeks, before the site was shutdown by Cloudflare.[144][145] This occurred shortly after the passage of H.R. 1865, FOSTA/SESTA, a set of bills that criminalized websites that “facilitate or support sex trafficking“, and was signed into law by President Donald Trump in 2018. According to The Verge, “The conflation of consensual sex work with sex trafficking, as well as the threat of litigation” led to a crackdown by Internet providers.[146] SESTA weakened protections for Internet infrastructure companies and was criticized on free speech grounds due to concerns about disproportionate impact and disruptions to the lives of sex workers.[147][148]
Switter’s parent company, Assembly Four, is based in Australia, where sex work has been decriminalized. They had hoped the social media platform would be safe from US legislation, but Cloudflare terminated service, saying the move was “related to our attempts to understand FOSTA, which is a very bad law and [sets] a very dangerous precedent”. In response, Assembly Four said that “Given Cloudflare’s previous stances of privacy and freedom, as well as fighting alongside the EFF, we had hoped they would take a stand against FOSTA/SESTA”.[144][149]
Response to the Russian invasion of Ukraine[edit]
After Russia invaded Ukraine in late February 2022 Ukrainian Vice Prime Minister Mykhailo Fedorov[150] and others[151] called on Cloudflare to stop providing its services in the Russian market amidst reports that Russia-linked websites spreading disinformation were using the company’s content delivery network services.[152] Cloudflare CEO Matthew Prince responded that “[i]ndiscriminately terminating service would do little to harm the Russian government but would both limit [Russian citizens’] access to information outside the country and make significantly more vulnerable those who have used us to shield themselves as they have criticized the government.”[153] The company later said it had minimal sales and commercial activity in Russia and had “terminated any customers we have identified as tied to sanctioned entities.”[154]
Cloudflare’s project Galileo, launched in 2014, offers NGOs DDoS protection for free. In 2022, they extended free protection to Ukrainian government and telecoms